Key Changes in ISO 27001:2013 to ISO 27001:2022 Controls
Information security is also constantly evolving, and to keep pace with the dynamic of cyber threats, standards such as ISO 27001 are regularly revised. The transition from ISO 27001:2013 to ISO 27001:2022 brings important changes, particularly to the controls organizations use to secure their information assets.
Changes in ISO 27001:2013 to ISO 27001:2022 Controls
The revisions aim to address new threats, incorporate best practices and improve the overall effectiveness of the standard in protecting sensitive information. Let's take a look at some key changes to the controls:
Adaptation to Modern Technologies
Given the rapid pace of technological development, ISO 27001:2022 introduces controls that specifically address modern developments. New controls cover areas such as cloud security, mobile device management and new technologies such as blockchain.
Enhanced Emphasis on Risk Management
In the 2022 version, there will be a greater focus on risk management across the ISMS.
Integration with Other Management Systems
ISO 27001:2022 is now more closely linked to other management system standards such as ISO 9001 (quality management) and ISO 14001 (environmental management).
This integration makes it easier for organizations to implement and maintain multiple management systems simultaneously.
Focus on Supply Chain Security
In view of the interconnectedness of business processes, the new controls pay particular attention to supply chain security.
Expansion of Incident Response Controls
ISO 27001:2022 extends incident response controls and ensures that organizations are well prepared to detect, respond to and recover from security incidents.
Cybersecurity Awareness and Training
Human factors continue to be a major source of vulnerabilities. The updated standard includes controls that further emphasize the importance of cybersecurity awareness and training for employees at all levels of the organization.
Transitioning to ISO 27001:2022
If your organization is currently certified to ISO 27001:2013, moving to the 2022 version will require a careful review and adaptation of your ISMS. It's important to conduct a gap analysis, update policies and procedures and ensure your team is familiar with the new 11 controls.
But don't worry - we'll help you with the transition!
New Controls in ISO 27001:2022
Organizational Controls in ISO 27001
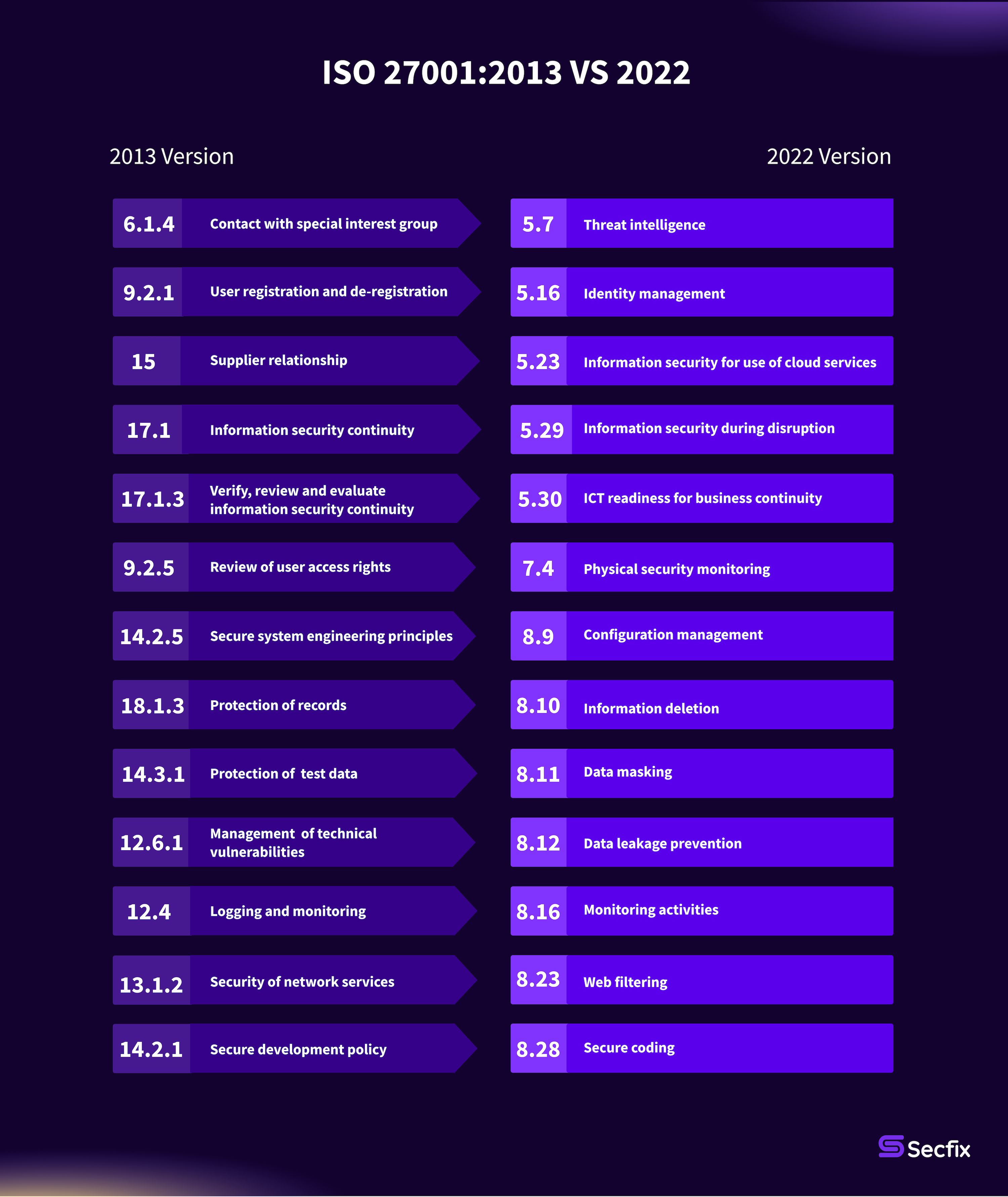
A 5.7 Threat Intelligence
A 5.7 has been formulated to help organizations understand their threat environment. This should enable them to identify appropriate measures to maintain information security in response to the threats identified.
A 5.23 Information Security for use of Cloud Services
A 5.23 introduces a control that describes processes for the acquisition, use, management and termination of cloud services that are tailored to an organization's specific information security requirements. This control enables organizations acting as "customers of cloud services" to formulate and oversee the information security policies relevant to cloud services. It serves as a preventative measure to mitigate risk by establishing information security policies and procedures for commercial cloud services.
A 5.30 ICT Readiness for Business Continuity
A 5.30 recognizes the critical role of ICT platforms and services in maintaining business continuity during disruptions or significant events.
Control 5.30 outlines an organization's recovery time objective (RTO) and business impact analysis (BIA) and describes the interplay between ICT services, these metrics and supporting controls.
Physical Controls in ISO 27001
A 7.4 Physical Security Monitoring
A 7.4 requires organizations to use appropriate monitoring tools. This is essential to detect and prevent the unauthorized entry of external and internal intruders into physically restricted areas.
Technological Controls in ISO 27001
A 8.9 Configuration Management
A 8.9, whether in the form of a standalone configuration file or a collection of linked configurations, defines the management of hardware, software and networks. For example, a firewall's configuration file encapsulates basic attributes that the device uses to regulate inbound and outbound network traffic and includes blocklists, port forwarding, virtual LANs and VPN details.
A 8.10 Information Deletion
A 8.10 describes how Organizations must be aware of their responsibility to securely delete data stored on internal servers, hard drives, arrays and USB drives when it is no longer needed. This obligation extends to data from employees, users, customers and the organization itself.
A 8.11 Data Masking
A 8.11 is a protection technique used to protect sensitive data, especially personal data, beyond an organization's standard security protocols, including access control.
The practice of data masking is often referenced in legal, statutory and regulatory guidelines that dictate the storage and access of employee, customer, user and vendor data.
A 8.12 Data Leakage Prevention
A 8.12 explains how Data leaks are characterized by unauthorized access, transmission or extraction of information by internal and external employees, systems or malicious entities targeting a company's information systems.
Organizations dealing with large amounts of data in various classifications on networked IT systems, applications and file servers are often faced with the problem of data leaks.
A 8.16 Monitoring Activities
A 8.16 is about effective network monitoring which is a critical component of successful IT support and information security operations.
Organizations should implement a comprehensive information security and incident response strategy that covers all aspects. This includes a proactive monitoring approach to prevent incidents before they occur and the coordination of reactive measures when required.
A 8.23 Web Filtering
A 8.23 additionally supports organizations in mitigating security risks and prevents threats such as malware infections from gaining access to external websites with malicious content.
A 8.28 Secure Coding
A 8.28 assists organizations in averting security risks and vulnerabilities resulting from inadequate software coding practices by establishing, implementing and evaluating secure software coding practices.
Examples of changes to the controls in ISO 27001:2022
A.6.1.5 ISO 27001:2013 → A 5.8 ISO 27001:2022
Information Security in Project Management expands on project management practices, emphasizing the integration of information security measures throughout the project lifecycle.
A.12.5.3 ISO 27001:2013 → A 6.9.6 ISO 27001:2022
Technical Vulnerability Management includes two sub-clauses dealing with vulnerability management. These sub-clauses are divided into technical management and guidelines for the organization's approach to software installations.
A.10.11 and 10.1.2 ISO 27001:2013 → A 8.24 ISO 27001:2022
Use of Cryptography enables organizations to maintain the confidentiality, integrity, authenticity and availability of information assets by properly applying cryptographic techniques and considering some special criteria.
A.15.1.3 ISO 27001:2013 → A 5.21 ISO 27001:2022
Managing Information Security in the ICT Supply Chain serves as a preventative measure in the ICT supply chain. It ensures risk mitigation by establishing an "agreed level of security" between the parties involved.
Secfix is happy to support you with your ISO 27011 certification or transition!
Book a consultation with us!







